...
Equipment installation
The installation work on the site should be guided by the general requirements and by the company's technical policy. Improperly executed, the installation can cause a violation of the entire network facility availability, the restoration of which may require a large time and financial resources.
In order to ensure the physical security, make perform the following settings for the wireless device:
- turn off the indicator lights on the device, it will increase its stealth;
- the unused ports of the wireless devices can be used by an attacker to gain access to the network, therefore, in order to eliminate the possibility of unauthorized connections, it is recommended to disable the unused network interfaces;
- the devices based on the H11 hardware platform support the PoE-out function on eth1. An attacker can use it to power third-party equipment. If the PoE-out function is not used, make sure it is disabled.
Facility operation
The installation quality control of the installation is carried out at in the stage phase of the acceptance into service of the device. The acceptance procedure should be performed in accordance with the company's technical policy.
Ensuring the information security is a continuous process that requires monitoring and response to identified and emerging threats, therefore, it is necessary to carry out preventive maintenance of for the communication facilities. Depending on the requirements established by the company and the specifics of the network node, the list of preventive measures may vary. A common set of regular jobs includes:
...
Wireless data transmission is performed in a shared environment, which brings a lot of possibilities for the attackers. The security measures described below should be applied in a comprehensive manner, since measures protecting from one threat may not be effective against another.
...
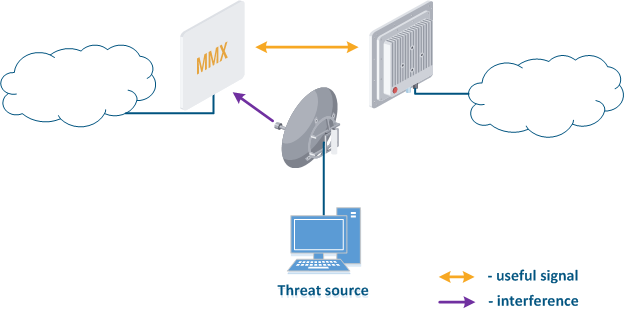
The frequency resource is limited, so the frequencies distributing process frequency distribution between wireless systems should be taken comprehensivelycarefully considered. Third-party wireless systems operating at on the same or on adjacent frequencies can affect the link (Figure 3). Usually, such an influence is not malicious, but it should be considered as a threat, since it leads can lead to the link operation failure. Our task is to search and select a frequency channel free of interference. Keep in mind that interference may not be present at the installation stage, but may appear during the wireless system operation.
Following The following actions can reduce the risks associated with this threat:
- Search for interference sources: devices of the InfiLINK 2x2 and InfiMAN 2x2 families allow you to obtain the MAC addresses of the systems operating in the selected frequency channel using the Radio scanner utility, it make . It is possible to identify the source of interference and to decide on the measures to eliminate its effect on the link.
- Manual spectrum scan: manual preliminary radio survey of the territory in which the communication system will be deployed. The frequency is selected taking into account the scan scanned data. Infinet devices allow to evaluate the state of the spectrum using the built-in "Spectrum analyzer" utilitytool.
- Auto spectrum scan: radio survey of the territory in which the communication system is deployed, performed periodically in automatic mode. The frequency channel can be automatically changed in accordance with the scan scanned data. Infinet devices support the DFS and iDFS technology technologies (see Dynamic Frequency Selection), which are designed to automatically scan the spectrum.
| Center |
|---|
Figure 3 - An example of a threat in the frequency channel |
Even if a the frequency channels distribution is coordinated, the problem of mutual interference may persist. That happens due to an out-of-band radiation: a radiation spectrum is not an ideal rectangle. It has side bands that affect adjacent frequency channels. Below are the spectra of two communication systems (Figure 4 a-b) which using adjacent frequency channels: in the first case (Figure 4a), the radiation power of the systems is equal and the threat attacking source's influence is lower than the communication system's sensitivity, in the second case (Figure 4b), the radiation power of the threat attacking source is higher than the one of the communication system and the out-of-band level is higher than sensitivity, it will affect the communication system's sensitivity, leading to interference in the interference formcommunication.
The automatic transmit power control (ATPC) function can help to reduce the influence of a third-party communication system on the used frequency channels. In case of interference, the devices with having ATPC active ATPC will increase the radiation power and keep maintain the link performance.
The link budget depends also on the used modulation-coding scheme: higher MCS MCSs require higher link parameters, therefore, they are impossible to use with a low signal level and a high level of interference. Thus, the modulation-code scheme selection is a compromise between the link performance and reliability. The automatic modulation control (AMC) function allows to select a the selection of the modulation-coding scheme in accordance with according to the current parameters of the radio and change it in accordance with the situationlink. This allows to increase increases the reliability and the availability of the information, by keeping the link operability operational even in strong interference conditions.
For more information about signals signal's frequency characteristics, proceed to the online course "Wireless Networking Fundamentals".
...
Authentication Settings
Popular scenarios of for the information confidentiality and integrity violation in a radio channel are the attacks of the Man-In-The-Middle type (MITM). Let's look at the examples of such attackattacks:
- Data interception (Figure 5a): the attacker installs a device that receives all transmitted signals in the communication system coverage area. All wireless systems use a shared data transmission medium, so devices receive data even if they are not specified as a recipients. Further, the device processes the frame at the L2 layer, if it is its recipient, or discards it if it is not. An attacker can pretend to be the recipient and gain an access to all messages, along with a legal addressee.
- Data relay (Figure. 5b): a specific case of the "Data interception" scenario in which an attacker uses a relay instead of a passive receiver. Such an attack option is applicable for example for point-to-point links with a narrow radiation pattern, where the Data Interception scenario is not suitable.
- Data spoofing (Figure 5c): a specific case of the "Data relay", in which the attacker changes data during relay. In such a scenario, not only confidentiality is violated but data integrity.
...