...
- Connection to an enterprise network (Figure 6): an attacker with a subscriber device can install it in the base station coverage area. After establishing a link with the base station sector, an attacker can gain access to the enterprise network and implement attacks aimed at integrity, availability and confidentiality violation. An attacker will be able to establish a link with a base station sector only if the an Infinet wireless device is used.
...
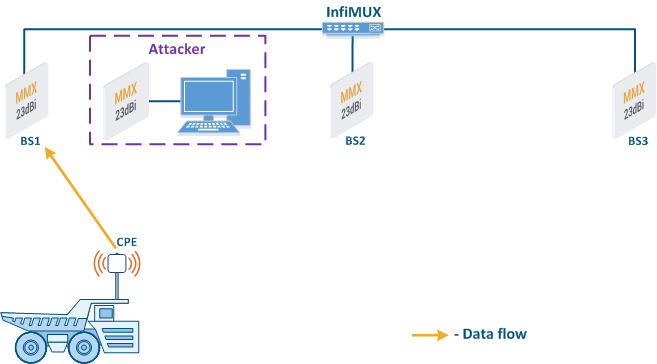
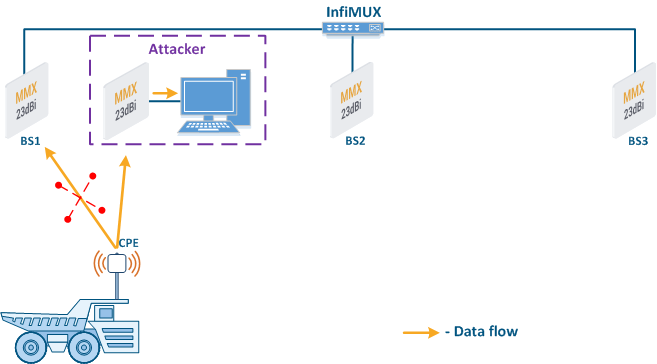
- Base station sector substitution (Figure 7a-b): an attacker installs a base station sector to which a subscriber station can connect. After that the attacker gains unauthorized access to the data originating from the subscriber station and to the network segment behind the subscriber station. Let's look at the example examples of such an attack in scenarios with the using mobile objects (see Connectivity with mobile objects). The A radio link is established between BS1 and the CPE (Figure 7a), the . The CPE is inttalled installed on the mobile object and breaks the connection while moving away from BS1 and starts to look for a new base station sector to set establish a connection (Figure 7b). An attacker set inserts a base station sector along the CPE's route, between BS1 and BS2, therefore, after disconnecting from BS1, the CPE establishes a connection with the attacker's sector. This attack type implementation is only possible only in case of disregarding the security settings disregarding.
| Center |
|---|
Figure 7a - Connection of the CPE station to the enterprise base station sector Figure 7b - Connection of the CPE station to the attacker's base station sector |
The Infinet devices use their own radio frame format, making it makes impossible to organize a establish communication between with any devices operating according to the 802.11 family standards and Infinet devices. This This complicates the attacker's plans, as he will be forced to use Infinet devices.
...
- Link ID: always change the default value to unique.
- Security key: devices can establish a connection only if they have the same link ID and security key, i.e. in order to reduce the likelihood of organizing establishing a link with an attacker's device, security keys must be installed on both devices.
- Authentication Mode: The InfiLINK 2x2 and InfiMAN 2x2 family devices support authentication mode settings when establishing a wireless link. "Static" and "remote" modes can limit the list of devices with which the link installation establishment is allowed. The static mode allows to set configure a list of devices MAC addresses of the devices with which a connection can be established (white list), or a list of addresses with which the connection establishment is forbidden (black list). The remote method allows to store MAC addresses for whitelists or blacklists centrally and perform appropriate requests when trying to establish a connection. Using one of the described authorization methods will significantly complicate an unauthorized connection of an attacker to the network.
- Max links: sets the maximum allowed number of connected CPEs. It is recommended to set the value of the actual subscriber stations number.
- Scrambling: reversible process of redistributing the data bits in accordance with according to a given algorithm in order to equalize the frequency spectrum of the signal. Scrambling also make makes it difficult to decrypt the intercepted data, because the attacker must have know the descrambling scrambling algorithm that was used in order to recover the original bit sequence. ScramblingThe scrambling/descrambling operations will require hardware resources, therefore it is recommended to use this option in cases of low hardware load.
- Frequency grid: the frequencies frequency range supported by the radio module can be deliberately limited using the frequency grid on all Infinet devices. This restriction narrows down the list of frequencies that can be set as central. The frequency grid additional effect is to increase the level of the device protection from against choosing a random frequency channel as a operational. If the automatic center frequency selection is set, then the device will select it in accordance with according to the grid. The center frequency can be set manually: on Master devices, the center frequency is set strictly, on Slave devices, depending on the family, either strictly or using one or more radio profiles. If a subscriber station uses several radio profiles (see Connectivity with mobile objects), then while connecting in order to connect to the base station sector, the profiles will be sorted scanned until finding a successful connectionparameter match.
- Global function: in scenarios with mobile objects, the Global option is used to connect a subscriber station to base stations sectors that are connected to the network core (see Connectivity with mobile objects). This approach can be used to block the CPE connections to base stations sectors installed by attackers (Figure 7b): since the attacker's base station is not connected to the network core, the subscriber station will ignore the attacker device during roaming.
...