...
The LLDP protocol is designed to exchange service information about a device with its directly connected devices. The service information is can be the VLAN ID, the MAC address, the device's name, the IP address of the management interface, etc. If an attacker will gain physical access to the device, then by launching the LLDP service on his PC, he will be able to get service obtain information about the device by exchanging service messages (Figure 13). This information can help the attacker to get unauthorized access to the device.
To prevent this type of attack, follow the these guidelines:
- Global LLDP disabling: if the technical policy of the company does not require the LLDP usage, it is recommended to disable its operation on all network devices.
- LLDP disabling on interfaces: if it is necessary to use LLDP, then it should be allowed only on those network interfaces to which network infrastructure elements are connected.
| Center |
|---|
Figure 13 - An example of the attack using LLDP |
SNMP
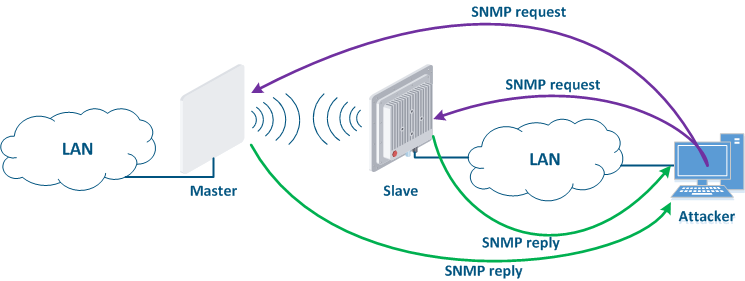
SNMP was created as a unified protocol for managing network devices and collecting data on about their state. The protocol provides for two types of requests: a request to GET some parameter value and a request to SET the specified parameter specified value. Thus, the devices that support SNMP can operate in read mode (only GET requests) and write mode (SET and GET requests). SNMP The SNMP server activation is necessary for centralized device management by using a monitoring system. But an attacker could take his chance if the SNMP server is not configured properly. In this case, he can not only get information about the network structure, but also change the configuration of the device (Figure 14).
To prevent unauthorized access follow the these guidelines:
- SNMPv3: by default, SNMPv1 and SNMPv2c support is activated on the devices , - a community with the name "public" is created. The SNMPv1 and SNMPv2c protocols provide authentication using the community name, which is openly transmitted over the network. SNMPv3 is recommended to use be used due to the implementation of authentication and of message encryption.
- Read only mode: if the SNMP SET mode is not used, then its support must be disabled. This will reduce the potential consequences of unauthorized access.
- White lists: Infinet devices allow to create white lists of access to the SNMP server.
| Center |
|---|
Figure 14 - An example of the attack using SNMP |
MINT
MINT is the proprietary Infinet protocol, whose operation can be organized in the wired and in the wireless segments. An attacker, gaining access to the MINT domain, can compromise all network devices related connected to this domain, therefore, pay special attention while configure when configuring the MINT protocol.
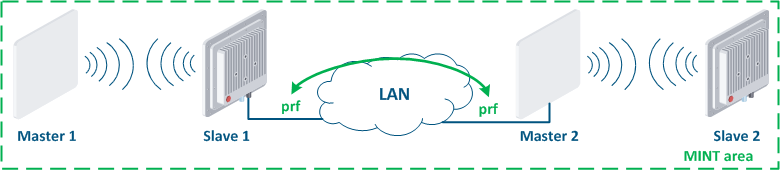
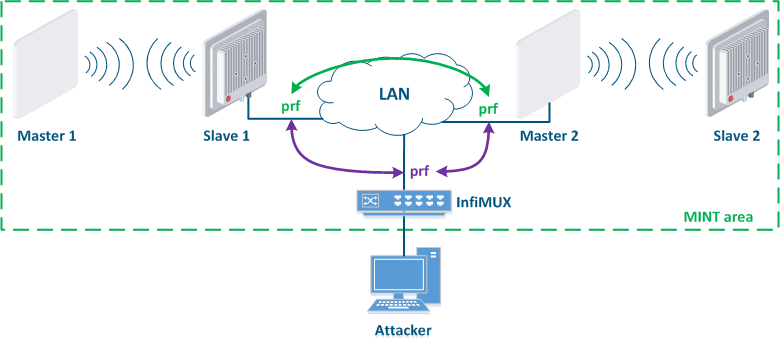
Let's look at the example of an attack using the MINT protocol: two wireless links Master 1 - Slave 1 and Master 2 - Slave 2 are joined into the a MINT area using PRF interfaces (Figure 15a). The attacker get gets physical access to the enterprise network using the InfiMUX switch, on which the a PRF interface is created (Figure 15b). PRF interfaces will establish communication channels between each other and all devices will be combined joined into a MINT area, so an attacker will receive information about the devices in this area and will be able to execute remote commands on them using MINT tools.
Protection against such attacks:
- Security key: the PRF interface is a virtual radio interface operating in a wired environment, therefore, same as for wireless interfaceinterfaces, the PRF interface supports the ability to install configure a security key. In this case, the link between two PRF interfaces will be organized established only if their security keys match.
- Password for remote commands execution: one of the MINT protocol tools is the ability to remotely execute commands on a device located in the same MINT area. By default, remote command execution is available without a password, set the . Set a password to limit the capabilities rights of the attacker.
| Center |
|---|
Figure 15a - Joining links in the MINT area Figure 15b - An example of the attack using the MINT protocol |
| Tip | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
...