The "General Security settings" section allows to configure basic system parameters, described in the table belowdevice access and security settings.
This section includes two main csubsectionsfollowing subsections:
Unit
...
Administrator access
Here you may change system administrator account login and password, to change the identification data, click the "Change admin password" button. We strongly recommend you to set a login and password after the first login to the device.
| Center |
|---|
| Scroll Title |
|---|
| title | Figure - Admin access |
|---|
| 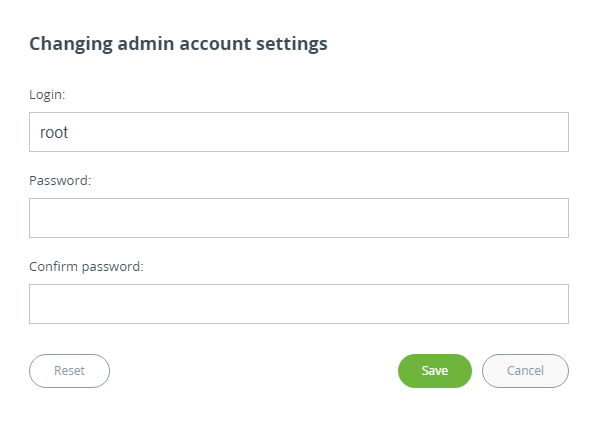 Image Added Image Added
|
|
Radius AAA
Here you may configure a device access control using a remote RADIUS server.
| Center |
|---|
| Scroll Title |
|---|
| title | Unit Radius server parameters description |
|---|
| | Parameter | Description |
|---|
| Device Name | The arbitrary wireless unit name which will be used by network administrators for unit identification. It will be shown in Web GUI side panel. | | Link ID | Wireless link identificator used to avoid connecting a unit to a wrong peer if there are several co-located units using the same center frequency. Specify different ID values for different links. Both ends of the same link must have the same ID. | | Access Key | Units at both ends of the wireless link should authorize each other before link establishment. Authorization is based on access keys: - Access key must be up to 64 characters long, without spaces;
- It must be the same at both ends of the link
| | Address | Set the RADIUS server IP address. | | Port | Set the RADIUS server port. | | Secret | Set the server password. |
|
|
| Center |
|---|
| Scroll Title |
|---|
| title | Figure - Unit RADIUS parameters |
|---|
| 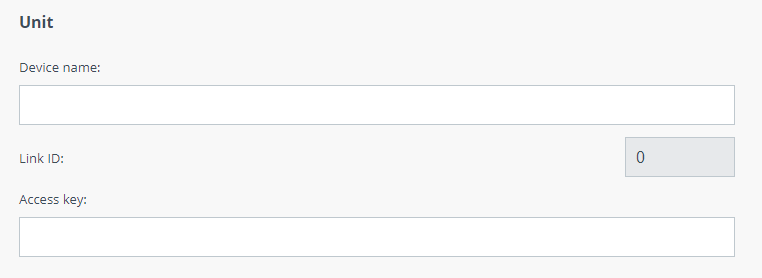 Image Removed Image Removed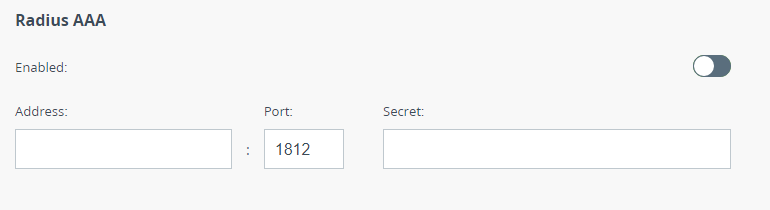 Image Added Image Added
|
|
Account
Here you may change system administrator account login and password.
...
...
Command line interface
Allows to enable / disable remote device control by the command line using Telnet and SSH protocols.
SSH (Secure Shell) protocol provides secure remote control to network devices. Its functionality is similar to the Telnet protocol, but, unlike Telnet, SSH encodes all protocol messages, including transmitted passwords. By default, only access via Telnet is enabled.
| Center |
|---|
| Scroll Title |
|---|
| title | Figure - Access protocols |
|---|
|  Image Added Image Added
|
|
Network access
This section is used to create a list of subnets from which access to the device will be allowed.
| Center |
|---|
| Scroll Title |
|---|
| title | Figure - Account parametersNetwork access |
|---|
|  Image Removed Image Removed
|
|
Regulatory domain
Regulatory domain automatically limits the wireless device operation which is may be needed to meet the local law requirements. Each regulatory domain may limits the following parameters:
- Range of available center frequencies
- Requirement of use LBT (Listen Before Talk) technique.
- Maximum EIRP (Equivalent Isotropically Radiated Power) value.
- Requirement of use radar detection technique.
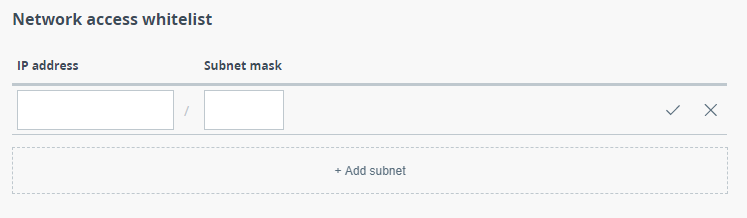 Image Added Image Added
|
|
Radio authentication settings
Units at both ends of the wireless link should authorize each other before link establishment. Access key must be up to 64 characters long, without spaces and must be the same at both ends of the link.
| Center |
|---|
| Scroll Title |
|---|
| title | Figure - Regulatory domain settings |
|---|
|  Image Removed Image Removed| Unit parameters description |
|  Image Added Image Added
|
|







