The information technology evolution has changed a human life in all spheres, making an information one of the most valuable resources. Same as other resources, information is valuable to its owner and can cause disputes and conflicts. That's why, to ensure information security is one of the important issues. The information systems development and the large amounts of data accumulation made necessary an integrated approach to ensuring the technical systems security.
The document describes information security tools in networks built using Infinet devices. Each wireless devices family has its own capabilities of application security tools, so at the end of a document section you will find links to technical documentation for each of the described tools.
Information security measures should be applied in accordance with the company IS policy. IS policy should take into account the following information characteristics:
An information security policy should include measures to ensure each of the basic information characteristics. If the described information characteristics aren't respected it may lead to financial, reputational and other loses. Remember that the IS policy realization is an endless process that requires periodic review of measures and their implementation check.
IS organization should be multilevel and not only realized with technical solutions. In addition to technical measures, legislative, administrative and procedural measures should be provided.
Measures to ensure IS are determined not only by the Infinet devices family, but also by the scenario of their use (Figure 1a-d). Let's look at several scenarios in which wireless devices connect network segments belonging to different responsibility areas, each area is characterized by a certain set of threats:
The security measures should correspond to existing risks, the IS architecture should not be redundant. For example, filtering of external connections should be performed at the interface on border with a third-party telecom operator, not on all intermediate nodes in networks.
The requirements for physical safety and security in the radio link are the same for all the scenarios beyond and are detaily described in the relevant sections. To configure devices, let's specify the following general requirements for information security:
The simplest scenario is joining two network segments located in the same responsibility zone (Figure 1a). Devices are used as a bridge, a simple connector in the LAN structure, therefore, the main information security tools are located at the boundaries of the left and right segments.
Figure 1a - Radio link joining two internal network segments |
In the scenario of joining two networks located in different responsibility areas, information security tools are realized on a radio device located at the border of two segments. A special example of the external network segment is the customer’s network, which is provided with a data service. In such scenarios, both inbound and outbound traffic should be filtered.
Figure 1b - Radio link connecting internal and external network segments
Figure 1c - Radio link connecting internal and external network segments |
The scenario where a wireless device is located at the border of the internal segment and the Internet is a special case of the previous scenario. The difference is in a low security on the device from the side of the Internet connection, that cause large number of risks.
Figure 1d - Radio link connecting internal network segments and Internet |
IS realization is achieved by the implementation of measures described in sections and subsections of IS:
The physical layer is the foundation of information security, so the devices physical security has a priority over company technical policy. Physical security should be comprehensive and include several components:
The communication node (including wireless devices) consists of three main elements (Figure 2):
Figure 2 - Communication node block diagram |
The site for the equipment placement must meet the requirements of the company technical policy and make the future communication node development possible. Following aspects should be taken into account while choosing a site:
An important factor of a site choosing is the ability to install auxiliary infrastructure elements, which will increase the availability of the communication system. Video surveillance and alarm systems are examples of auxiliary infrastructure. An alarm allows quickly detect an unauthorized access to the object, and a video surveillance system will be useful in investigating incidents.
Installation work on the site should be guided by the general requirements and company technical policy. Improperly executed installation can cause a violation of the entire network facility availability, the restoration of which may require large time and financial resources.
In order to ensure physical security, make the following settings for your wireless device:
Installation work quality control is carried out at the stage of object acceptance into service. The acceptance procedure should be performed in accordance with the company technical policy.
Ensuring information security is a continuous process that requires monitoring and response to identified and emerging threats, therefore, it is necessary to carry out preventive maintenance of communication facilities. Depending on the requirements established in the company and the specifics of the network node, the list of preventive measures may vary. A common set of regular jobs includes:
| |||||||||||||||||||||||||||||||||||||||||||
Wireless data transmission is performed in a common environment, which brings a lot of possibilities for attackers. The security measures described below should be applied in a comprehensive manner, since measures protecting from one threat may not be effective against another.
The frequency resource is limited, so the frequencies distributing process between wireless systems should be taken comprehensively. Third-party wireless systems operating at the same or adjacent frequencies can affect the link (Figure 3). Usually, such an influence is not malicious, but it should be considered as a threat, since it leads to the link operation failure. Our task is to search and select a frequency channel free of interference. Keep in mind that interference may not be present at the installation stage, but may appear during the wireless system operation.
Following actions can reduce the risks associated with this threat:
Рисунок 3 - Пример угрозы в частотном канале системы |
Even if a frequency channels distribution is coordinated, the problem of mutual interference may persist. That happens due to an out-of-band radiation: a radiation spectrum is not an ideal rectangle. It has side bands that affect adjacent frequency channels. Below are the spectra of communication systems (Figure 4 a-b) which using adjacent frequency channels: in the first case (Figure 4a) the radiation power of the systems is equal and the threat source influence is lower than the communication system sensitivity, in the second case (Figure 4b) the radiation power of the threat source is higher than communication system and the out-of-band level is higher than sensitivity, it will affect the communication system in the interference form.
The automatic transmit power control (ATPC) function can help to reduce the influence of a third-party communication system on the used frequency channels. In case of interference, devices with active ATPC will increase the radiation power and keep the link performance.
The link budget depends also on the used modulation-coding scheme: higher MCS require higher link parameters, therefore, they are impossible to use with a low signal level and a high level of interference. Thus, the modulation-code scheme selection is a compromise between the link performance and reliability. The automatic modulation control (AMC) function allows to select a modulation-coding scheme in accordance with the current parameters of the radio and change it in accordance with the situation. This allows to increase the reliability and availability of information, by keeping the link operability even in strong interference conditions.
For more information about signals frequency characteristics proceed to the online course "Wireless Networking Fundamentals".
Figure 4a - An example of an adjacent frequency channel influence on a communication system
Figure 4b - An example of an adjacent frequency channel influence on a communication system |
Popular scenarios of the information confidentiality and integrity violation in a radio channel are attacks of the Man in The Middle type (MITM). Let's look at the examples of such attack:
Figure 5a - Data interception
Figure 5b - Data relay
Figure 5c - Data spoofing |
Also scenarios of obtaining unauthorized access to resources through a connection to a radio network are possible. Let's look at the examples of such attack:
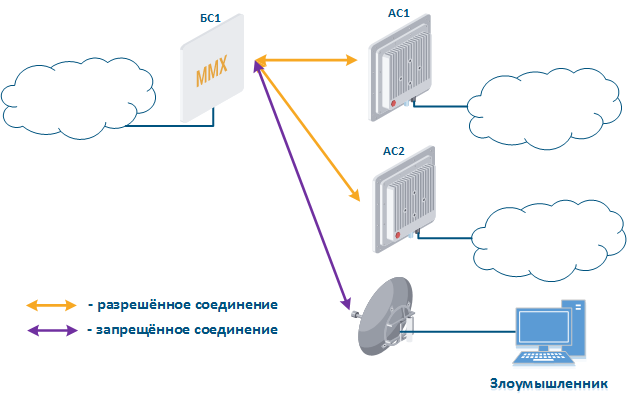 Figure 6 - Connection to an enterprise network |
Figure 7a - Connection of the CPE station to the enterprise base station sector
Figure 7b - Connection of the CPE station to the attacker base station sector |
Infinet devices use their own radio frame format, it makes impossible to organize a communication between devices operating according to the 802.11 family standards and Infinet devices. This complicates the attacker's plans, as he will be forced to use Infinet devices.
To counter such attacks, the following options should be used:
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Unauthorized access to the device management interface is a serious threat that can lead to a violation of all the basic data properties, measures to ensure information security and reduce potential risks should be elaborated carefully.
By default, one user is added to the configuration with administrative rights and the following login values:
Since the default authentication settings allows a high probability of unauthorized access, change the username and password during initial setup. |
A company can have several lines of technical support: in such scheme, some problems that do not require wireless devices reconfiguration can be solved by the first line of technical support. Thus trivial tasks can be solved without qualified employees of the second and third lines of technical support. To implement this scenario, a guest account can be added to the device configuration. A user which has access to the management interface using a guest account can use the utilities and view interface statistics, but he is not allowed to make configuration changes.
It is recommended to use centralized account storage for networks with a large number of devices. This allows to avoid errors when blocking accounts, provide a single password policy and have a single interface for accounts management. Infinet devices support the RADIUS protocol, which is intended for centralized authentication, authorization and account management in networks. Depending on the capabilities and scale of the network, the database for RADIUS operation can be deployed on a separate device, or combined with other network elements.
The algorithm for a RADIUS server usage is following (Figure 8):
|
Infinet devices can be configured using the Web GUI or the command line interface (CLI). Some parameters can only be configured via CLI. Access to different interfaces is carried out using various network protocols. It is recommended to disable unused protocols, to reduce the possibility of unauthorized access to the device management interface.
The management protocols supported by Infinet devices correspond to the management interfaces in a following way:
The network management interface (mgmt), which used to access the device is organized differently in different device families:
In addition to selecting the the management interface, it is also possible to control the connectivity between the management interface and other network interfaces. This mechanism allows to restrict access to the device via wired or wireless interfaces, depending on the scenario.
Figure 1 demonstrates the scenarios for Infinet devices usage. Let's look at the device management configuration for each scenario. To do this, we have added the PCs connected to different network segments to perform the devices management (Figure 9a-c):
Figure 9a - Radio link joining internal network segments
Figure 9b - Radio link connecting internal and external network segments
Figure 9c - Radio link connecting internal network segment with Internet |
We recommend to use the following principles of management configuration:
InfiLINK 2x2, InfiMAN 2x2 and Quanta 5 family devices allows to create white access lists. In this case only network nodes which IP addresses mentioned in the list will be permitted to access the management interface.
ERConsole utility is used to restore an access to all Infinet devices (see the "ERConsole" screencast). The utility can be used for the following purposes:
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||
Data transmission is the main function of any network equipment. In addition to user data, devices exchange service messages of auxiliary protocols such as SNMP, LLDP, etc. The described functions implementation contains potential threats that an attacker can use, and requires accurate configuration of all wireless devices subsystems.
Wireless systems are hardware and software systems. Therefore, one of the most important requirements is the timely software updating. It is recommended to use stable software versions and monitor the release of updates. Used software version can be checked directly on the device.
When making changes to the devices configuration, keep in mind that the mechanism for applying the settings depends on management interface used:
In some cases, errors made during the device configuration process can lead to access loss to the device and the device may need to be reset to factory settings (see "Access recovery"). To reduce the risk of this scenario, it is recommended to use a delayed device reboot. In this case, after applying the new configuration, a device availability check will be performed. If the device is unavailable, the previous version of the configuration will be restored.
By default, switching on the device is configured to pass data between the wired and wireless interfaces without filtration. Such scheme is vulnerable to a large amount of spurious traffic, which can take up all the available throughput and the link will actually become inaccessible for the transmission of useful traffic. An example of spurious traffic is a broadcast storm, which can cause errors in devices switching. Measures to protect the network infrastructure from such attacks are:
In addition to user data, devices exchange service messages of auxiliary protocols.The security should take into account that any available service is a potential attacker's target.
Infinet devices can be configured as a DHCP client, DHCP server and DHCP relay. Keep in mind that the DHCP protocol supports not only the IP address allocation, but also the network settings transmission.
Let's look at the example of the attack using the DHCP (Figure 10): there is link between the Master and Slave, a DHCP client is activated on the Slave device radio interface and the DHCP server is installed on the corporate network. In this example the attacker managed to connect the network device on which the DHCP server is configured to the corporate network. After the Master-Slave link has been established, the Slave device sends a broadcast request to the network to receive network settings from the DHCP server. DHCP servers located on the network respond to a request from Slave. If the response from the attacker server is received first, the Slave device will assign to the network interface the proposed address and network settings that are transmitted in this request. Thus, an attacker can set his device as the default router and gain access to the traffic transmitted by the Slave device.
Figure 10 - An example of the attack using the DHCP |
An attacker’s device can also act as a DHCP client (Figure 11): the functions of network DHCP server are implemented on Infinet device, an attacker’s device is connected to the network. In a situation where the DHCP server configuration protocol does not provide security measures, the attacker will generate a request and the server will provide the device with network details. Thus, an attacker will gain access to data transmitted over the network.
Figure 11 - An example of the attack using the DHCP |
In order to increase the security of using DHCP in the corporate network, it is recommended to implement the following measures:
Поскольку протоколы Ethernet и IP относятся к разным уровням модели сетевого взаимодействия, то необходим инструмент, который будет связывать адреса устройств, используемых в каждом из протоколов. Таким инструментом является протокол ARP и заполняемая им таблица соответствия адресов. Таблица состоит из записей, в которых MAC-адрес интерфейса сопоставлен с IP-адресом, что используется при передаче IP-пакетов, инкапсулированных в Ethernet-кадры.
Рассмотрим пример атаки с подменой IP-адреса: через радиоканал Master-Slave организован доступ к сети интернет двум клиентам (Клиент 1 и Клиент 2). За каждым из клиентов закреплён IP-адрес, который является идентификатором для назначения тарифного плана. Клиенту с адресом 192.168.0.1 предоставляется пропускная способность 10 Мбит/с, клиенту с адресом 192.168.0.2 - 2 Мбит/с (рис. 12а). В какой-то момент времени Клиент 1 выключает ПК и не пользуется услугами провайдера, в это же время Клиент 2 заменяет свой IP-адрес на IP-адрес 192.168.0.1, закреплённый за Клиентом 1 (рис. 12б). В этом случае Клиент 2 получит доступ в Интернет с большей пропускной способностью, и у Клиента 1, после включения, возникнут проблемы с доступом к сети.
Рисунок 12а - Пример атаки с подменой IP-адреса
Рисунок 12б - Пример атаки с подменой IP-адреса |
Рассмотренный вид атак с подменой IP-адреса можно предотвратить, добавив статическую запись в таблицу соответствия адресов протокола ARP. В этом случае, после смены IP-адреса данные Клиента 2 передаваться не будут, т.к. за адресом 192.168.0.1 будет закреплён MAC-адрес Клиента 1.
Протокол LLDP предназначен для обмена справочной информацией об устройстве с непосредственно подключенным к нему устройством. В качестве справочной информации передаётся имя VLAN, MAC-адрес, имя устройства, IP-адрес интерфейса управления и т.д. В случае, если злоумышленник получит физический доступ к устройству и подключится к нему, то, запустив на своём ПК службу LLDP, сможет, обменявшись служебными сообщениями, получить справочную информацию об устройстве (рис. 13). Эти сведения могут облегчить ему задачу по несанкционированному доступу к устройству.
Для того, чтобы предотвратить атаки данного типа, необходимо придерживаться следующих правил:
Рисунок 13 - Пример атаки с использованием протокола LLDP |
Протокол SNMP был создан как унифицированный протокол для управления сетевыми устройствами и сбора данных об их функционировании. Протокол предусматривает запросы двух типов: запрос GET для получения значения какого-либо параметра и запрос SET для установки параметра в указанное значение. Таким образом, устройства, на которых реализована поддержка SNMP, могут работать в режиме чтения (обрабатывать только запросы GET) и режиме записи (обрабатывать запросы SET и GET). Активация сервера SNMP необходима, как правило, для централизованного управления устройствами с помощью системы мониторинга. Но если сервер SNMP настроен недостаточно надёжно, то им может воспользоваться злоумышленник В этом случае он сможет не только получить информацию о структуре сети, но и изменить конфигурацию устройства (рис. 14).
Для предотвращения несанкционировнного доступа cледуйте рекомендациям:
Рисунок 14 - Пример атаки с использованием протокола SNMP |
MINT является фирменным протоколом компании Инфинет, работа которого может быть организована в проводном и беспроводном сегментах. Злоумышленник, получив доступ к области MINT, может cкомпрометировать все сетевые устройства, относящиеся к этой области, поэтому при использовании протокола MINT необходимо обратить особое внимание на его настройку.
Рассмотрим пример атаки с использованием протокола MINT: два беспроводных канала связи Master 1 - Slave 1 и Master 2 - Slave 2 объединены в область MINT с помощью интерфейсов PRF (рис. 15а). Злоумышленник, имея физический доступ к сети предприятия, подключается к ней коммутатором InfiMUX, на котором создан интерфейс PRF (рис. 15б). В общем случае, интерфейсы PRF установят между собой каналы связи и все устройства будут объединены в область MINT, поэтому злоумышленник получит информацию об устройствах в этой области и сможет выполнять удалённые команды на них средствами MINT.
Средства защиты от атак подобного типа:
Рисунок 15а - Объединение каналов связи в единую область MINT
Рисунок 15б - Пример атаки с использованием протокола MINT |
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Инфраструктурная безопасность - это важнейший раздел информационной безопасности, которому не всегда уделяется должное внимание. Состав инфраструктуры зависит от технической политики предприятия. В сети должны быть реализованы средства журналирования, мониторинга и технического учёта (ТУ).
Система мониторинга необходима для централизованного управления устройствами и контроля работы сети. Кроме того, система мониторинга рассылает уведомления инженерам, если значения параметров вышли за рамки разрешённого диапазона. Такие уведомления уменьшают время реакции обслуживающего персонала, благодаря чему минимизируются последствия сбоев и вероятных атак.
Системы мониторинга могут быть интегрированы с системами сигнализации и видеонаблюдения.
Компания Инфинет предоставляет собственную систему мониторинга беспроводных устройств Инфинет - InfiMONITOR. Система мониторинга осуществляет сбор данных следующими способами (рис. 16):
Рисунок 16 - Обмен данными между устройствами и системой мониторинга |
Детальное расследование инцидентов требует анализа системных журналов, зарегистрированных на устройстве. Устройства Инфинет поддерживают логирование событий, однако системный журнал событий не сохраняется после перезагрузки устройства. Кроме того, в крупных сетях удобно иметь централизованное хранилище журнальных файлов, потому что такое хранилище предоставляет интерфейс просмотра журналов всех сетевых устройств, используемые при расследовании инцидентов.
Для этих целей в сети выделяется сервер Syslog. Все журнальные записи одновременно с записью в системный журнал отправляются на сервер Syslog (рис. 17). Это позволяет хранить историю сообщений всех сетевых устройств централизованно и не зависеть от состояния системного журнала непосредственно на устройстве, который может быть очищен при перезагрузке или несанкционированном доступе.
Рисунок 17 - Обмен данными с Syslog-сервером |
Решение эксплуатационных задач требует от инженеров комплексной информации об устройствах для получения доступа на объект, восстановления конфигурации, добавления в систему мониторинга и т.д. Такая информация включает в себя как технические, так и административные аспекты. Для того, чтобы эти данные хранить и иметь к ним доступ, в сети могут быть использованы специализированные системы технического учёта. Системы технического учёта содержат следующую информацию:
| |||||||||||||||||||||||||||||||||||||||||||||||||